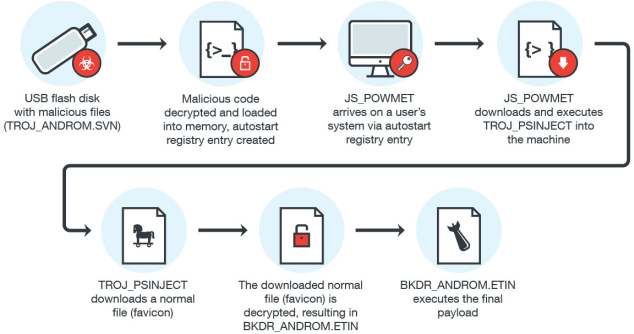
Android for Hackers: How to Backdoor Windows 10 Using an Android Phone & USB Rubber Ducky « Null Byte :: WonderHowTo

Android for Hackers: How to Backdoor Windows 10 Using an Android Phone & USB Rubber Ducky « Null Byte :: WonderHowTo

Amazon.com : Complete AC/ DC Power Kit for GoPro Hero 3+ and Hero 4 (Not compatible with Hero 3 & older) Includes USB Power Cable,Water-resistant Backdoor Passthrough,and 3 Adapter Plugs (US &

Mandiant details UNC4191 cyber espionage activity using USB devices as initial infection vector - Industrial Cyber

Android for Hackers: How to Backdoor Windows 10 Using an Android Phone & USB Rubber Ducky « Null Byte :: WonderHowTo

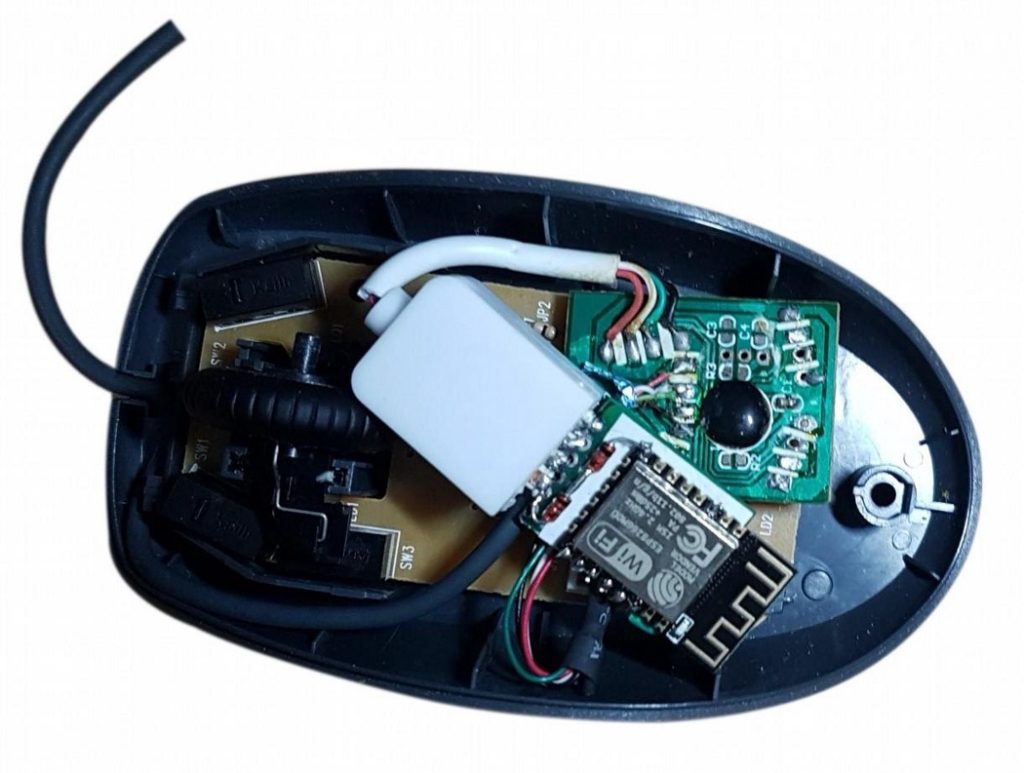
Evil Maid" Firmware Attacks Using USB Debug - Eclypsium | Supply Chain Security for the Modern Enterprise

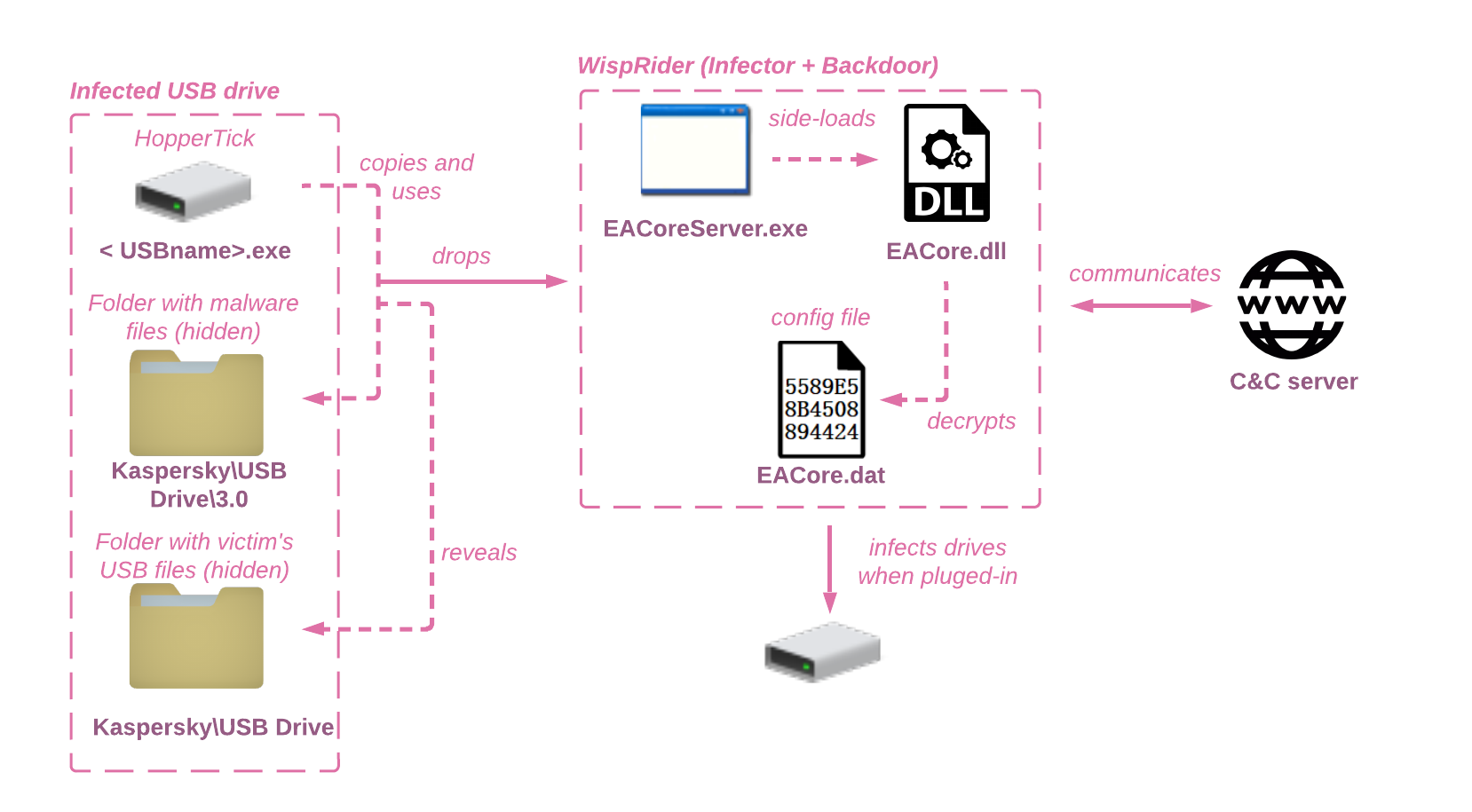
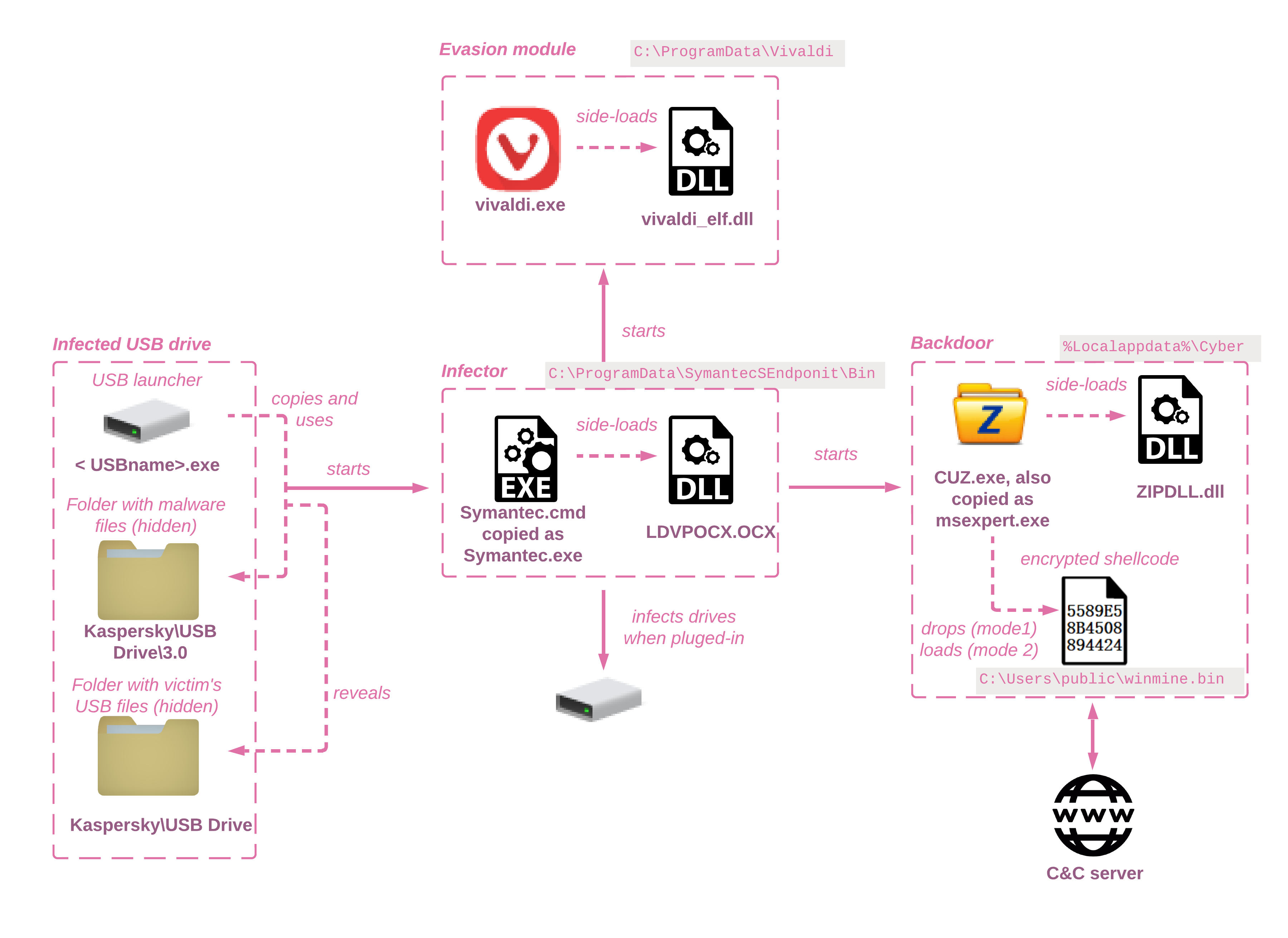
Stealthy USB: New versions of Chinese espionage malware propagating through USB devices found by Check Point Research - Check Point Blog

Amazon.com: Yubico YubiKey 5C - Two Factor Authentication USB Security Key, Fits USB-C Ports - Protect Your Online Accounts with More Than a Password, FIDO Certified : Electronics